Dear Mudita Kompakt Team @urszula @Michal_Kicinski @aleksander,
NA devices were delivered last week, placing all users within the 14-day return window. Some critical questions have not been answered.
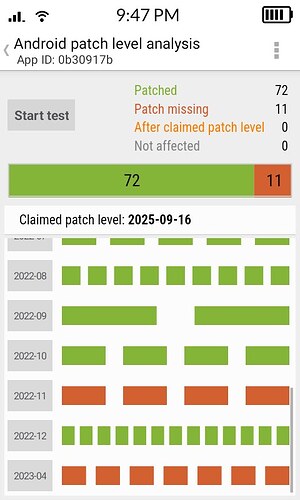
Kompakt Operating System Security - AOSP 12 No Longer Supported
We need a definitive yes or no answer: Will the AOSP version be upgraded to Android 13 or 14 to enable monthly security patches?
If no, will security patches be backported to the AOSP 12 in a transparent and timely manner?
If both answers are no, this creates serious security implications that need to be addressed. Users have not been warned about the severe security risks of using an unpatched device.
Many users have already sideloaded sensitive apps like Signal and financial apps without understanding these risks.
While sideloaded apps are “officially unsupported”, Bluetooth, WiFi, SMS, and other core system components (WebView browser) present equally serious attack vectors on unpatched devices.
At minimum, security patches for these domains need to be backported.
Will the Mudita OS development team commit to a public bug tracker?
This forum is not a substitute for a bug tracker. Users should not be burdened with hunting for acknowledgment of reported issues.
Creating a public bug tracker will:
- Eliminate duplicate bug reports across multiple forum threads
- Highlight prioritized bugs without requiring commitment to timelines
- Provide users a straightforward overview of platform status
Without clear answers to the above questions, users cannot make informed decisions about keeping their devices. I hope to hear back from the team soon.
Thank you.